One of the many perks of Hacker School is alumni Thursdays, where alumni can come in to hack on open source projects and pair program with others. However, there is a problem — Hacker School doesn't have enough key fobs to give to every alumnus. Instead, they ring the doorbell, and someone sits by the phone to press the "unlock" button whenever it rings.

The phone in question. The lowest of the three buttons unlocks the building's front door.
This is a poor solution — the doorbell is loud and buzzy, and whoever has to sit by the phone is constantly distracted. This is Hacker School, dammit! We can fix this! Since Hacker School seems to always have a surplus of Arduinos, J.J. and I set out to connect an Arduino to the phone. We could use this Arduino with Twilio to let alumni unlock the door with a text message.
Hacking the Phone
With the help of Carl's disassembling skills and a butter knife, we got the phone opened up.

There was some label that said "WARNING: HIGH VOLTAGE, MAY CAUSE MORTAL DAMAGE", but we just kinda ignored it.

The phone was surprisingly difficult to disassemble, but we managed to expose the part of the phone just behind the buttons in a way so that everything still worked. Simulating a press of the "unlock" button was as simple as connecting a wire from one metal contact to another. The phone manufacturer even put in little metal rings that made it easy to connect alligator clips. How considerate of them!

The two metal contacts behind the button.
We obviously didn't want to have someone standing there connecting and disconnecting wires to unlock the door, so we used a relay hooked up to one of the Arduino's output pins to programmatically allow current to flow across the button. J.J. has a soon-to-be published blog post with more details.

Once the relay was set up, the Arduino could unlock the door, but had no idea when to. We got an ethernet shield, and J.J. created an HTTP server for the Arduino that unlocked the door whenever it received a POST with the correct password. (I'll write more about how we encrypted that password in a future blog post.)

The finished Arduino and phone, all packaged up neatly. The note on the screen reads "Mess with the best, die like the rest."
Twilio and Authentication
We wanted to design the text messaging system so that only Hacker Schoolers with registered phone numbers could unlock the door. Rather than overload the already memory-starved Arduino with more tasks, we decided to have a separate server, on an actual Linux-running computer, to handle the user registration and text messaging. When the server detects a new text message from a Hacker Schooler, it sends a HTTP POST to the Arduino, and the Arduino unlocks the door.
Originally this server was to be hosted on Heroku. Sadly, that would require poking a hole in the Hacker School firewall for Heroku to send unlock requests to the Arduino. Instead, we hosted the server locally on the Hacker School network. Although this forces people to connect to the Hacker School Wi-Fi to register their phone numbers, it makes the whole setup a bit more secure, so we stuck with it.
We wrote this server, called Doorbot, in Sinatra. When someone first connects, Doorbot uses Hacker School's OAuth server and the oauth2 Ruby gem to make sure they're a Hacker Schooler.
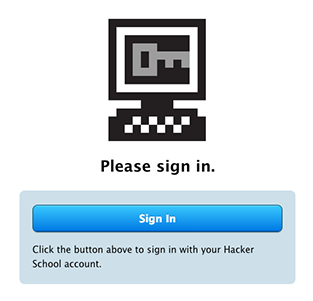
After people have logged in with their Hacker School account, Doorbot prompts them to add their phone number to the whitelist.
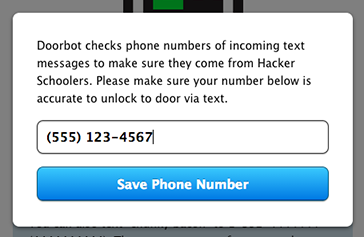
There's also a web interface to unlock the door with the click of a button.
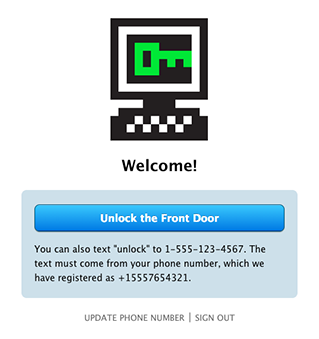
After someone registers their phone number, they can text Doorbot to unlock the door. To check for incoming texts, Doorbot has a separate Ruby script which queries Twilio every couple of seconds. Twilio recommends using their callback system to notify a server when texts are received, but since this is hosted on a local network, Twilio can't connect to Doorbot. We had to settle for a polling method, which uses the Twilio API to check the SMS logs every couple of seconds. When a new text appears in the log, Doorbot makes sure it comes from a registered number, and then tells the Arduino to unlock the door.
The Result
After about a week and a half of on and off work, we've ended up with a reliable server and Arduino setup to let in alumni without key fobs. Hacker Schoolers can text a number, and the front door unlocks within a second or two. It's fun, and I like to think it makes Hacker School a little more welcoming for alumni every Thursday. This project has also been really educational, both in terms of how to control an Arduino remotely with HTTP, as well as how to cope with tight memory constraints.
If you'd like to run your own Doorbot/Doorduino pair, feel free to clone them on Github. You'll have to modify Doorbot to not require Hacker School OAuth, but that shouldn't be too difficult, and you should be up and running in no time at all.
...or for a change of pace, perhaps you'd enjoy my other blog Agoraphobia →